Contents
- DORA implementation
- Governance and organisation
- Information risk and information security management
- IT operations
- ICT business continuity management
- ICT project management and application development
- ICT third-party risk management
- Operational information security
- Identity and access management
- Annex: Minimum contractual clauses
DORA implementation
Governance and organisation
| Area/Topic | DORA Requirement | Difference to BAIT/VAIT |
|---|---|---|
| Strategy | Mandatory DOR Strategy | BAIT/VAIT require IT Strategy; DORA introduces a separate ICT-resilience-focused strategy |
| Governance | ICT governance integrated into enterprise-wide risk mgmt. | BAIT/VAIT focus on information security governance |
| Roles | ICT risk control function + ICT third-party monitoring function | BAIT/VAIT only require ISO; no explicit third-party monitoring role |
| Management Body | Strong, explicit, prescriptive responsibilities and required ICT competence | BAIT/VAIT are less detailed; no explicit training requirement |
| Policies | Mandatory approval of multiple ICT-specific policies | BAIT/VAIT do not mandate policy approval at board level |
Information risk and information security management
| Area/Topic | DORA Requirement | Difference to BAIT/VAIT |
|---|---|---|
| Information Security Integration | Fully embedded in ICT risk management | Board-level approval and oversight |
| Security Policies | Explicit and mandatory policies | Must be risk-aligned and documented |
| Classification & Handling | Formal info classification scheme | Applies to entire lifecycle |
| IAM | Strong MFA, privilege mgmt, SoD | Automated processes expected for larger firms |
| DLP & Safe Data Handling | Prevent leakage; environment separation | Productive data in test systems only with strict controls |
| Logging & Monitoring | Comprehensive logs; SIEM-level detection | Logs must be integrity-protected |
| Cryptography | Strong encryption & key mgmt | Legacy algorithms discouraged |
IT operations
| Area/Topic | DORA Requirement | Difference to BAIT/VAIT |
|---|---|---|
| Operational stability | Updated, reliable, technologically resilient ICT systems; stress-phase ability | Significantly stronger; stress-phase capability new |
| Legacy systems | Annual + event-driven risk assessments | New mandatory frequency |
| System & info classification | Full ICT system + information inventory with dependencies | Holistic model, new scope |
| Change management | All changes in scope, no threshold | Major expansion, largest impact |
| Backups | Policy + segregated systems + reconciliation | Stronger than previous requirements |
| Restoration | CIA+A protection ensured during restore | New legal requirement |
| Testing | Mandatory, scenario-based | More extensive than BAIT/VAIT |
ICT business continuity management
| Area/Topic | DORA Requirement | Difference to BAIT/VAIT |
|---|---|---|
| Core document | Formal ICT business continuity policy | No explicit ICT BCM policy term |
| Plans | ICT BCM plans + ICT response & recovery plans | IT contingency / continuity plans |
| Scenarios | Climate, insider, political instability, data-location risks, power outages explicitly required | Generic disruption scenarios |
| Governance | Management body approves & oversees ICT BCM; annual review & testing | Board role less explicit |
| Testing | Annual + event-driven; includes crisis communication plans | Annual/regular, no explicit crisis-comms testing |
| Crisis function | Dedicated crisis management function for ICT incidents | Not explicitly required |
ICT project management and application development
| Area/Topic | DORA Requirement | Difference to BAIT/VAIT |
|---|---|---|
| Project methodology | Minimum mandatory elements | High-level governance |
| Documentation | Less documentation required | Extensive |
| Secure development | Highly prescriptive (secure coding, environments) | General |
| Source-code testing | Mandatory SAST/DAST for internet-facing systems | Not explicitly required |
| Third-party code | Mandatory anomaly testing | Not explicitly required |
| EUC tools | Fully included | Separate regime |
| Change management | All changes | Only significant changes |
| Separation of duties | Mandatory | Required |
| Testing requirements | Detailed, structured, mandatory | Less specific |
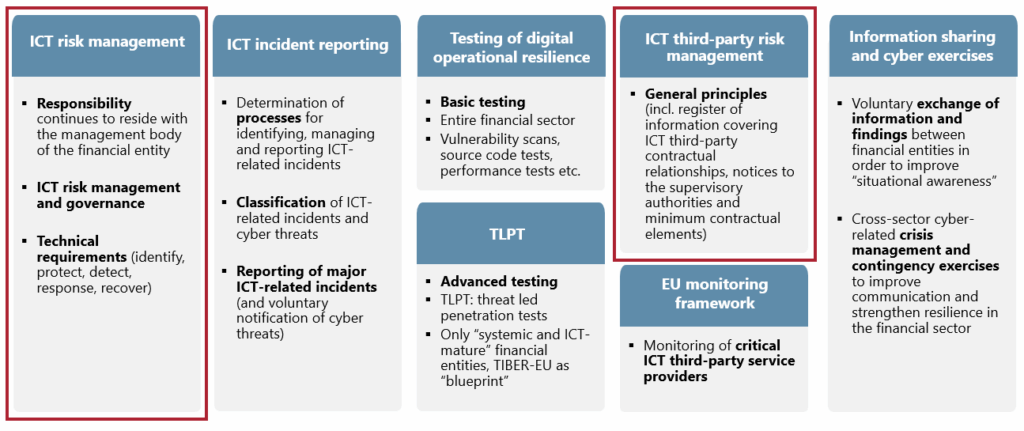
ICT third-party risk management
| Area/Topic | DORA Requirement | Difference to BAIT/VAIT |
|---|---|---|
| Scope | ICT third-party regime for all ICT services supporting business operations | BAIT/VAIT mainly cover outsourcing; many ICT vendors previously out of scope |
| Outsourcing Link | ICT TPRM supplements MaRisk/MaGo outsourcing rules | Before: only sectoral outsourcing; no parallel EU ICT layer |
| Critical / Important Functions | Classification of ICT services for critical or important functions (CIF) | BAIT/VAIT work with material outsourcing; CIF is a new ICT-specific lens |
| Contractual Content | Detailed minimum clauses for all ICT contracts + extra set for CIF | BAIT/VAIT clauses more generic, less ICT-specific and less prescriptive |
| Subcontracting | RTS SUB with rules for chains, notice, objection and termination | Sub-outsourcing only broadly addressed; no ICT-specific chain rules |
| Risk Analysis & Due Diligence | Standardised, expanded risk & provider assessment, incl. concentration | Existing due diligence narrower, no harmonised ICT risk catalogue |
| Exit & Concentration | Tested exit plans and explicit ICT concentration risk management | Exit often waived intra-group; concentration not as central and detailed |
| Governance & Register | Board-approved ICT TPRM policy, monitoring role and information register | No specific ICT-TPRM policy/role; no ICT-wide register requirement |
Operational information security
| Area | DORA Requirement | Difference to BAIT/VAIT |
|---|---|---|
| Network security | Legally binding minimum network security controls | Good practice framework |
| Detection | Comprehensive, correlated, multi-layer detection tools (SIEM-equivalent) | General expectation |
| Alert management | Alerts must route to ICT security | Not formally regulated |
| Vulnerability mgmt. | Mandatory structured vulnerability lifecycle (ID → Assess → Remediate → Verify) | General controls |
| Logging | Mandatory integrity-protected logging for all critical events | Strong expectation |
| Coverage | Full-environment coverage (on-prem, cloud, hybrid) | Risk-based |
| Governance | Direct integration with ICT risk mgmt. + board oversight | CISO involvement |
Identity and access management
| Area/Topic | DORA Requirement | Difference to BAIT/VAIT |
|---|---|---|
| Scope | Separate identity management (Art. 20) and access management (Art. 21) | BAIT/VAIT bundle IAM; split is not made explicit |
| Identity Management | Formal identity management guidelines and procedures | Identity aspects implicit, not a standalone regulated topic |
| Unique IDs & Lifecycle | Unique IDs for all users (incl. third-party staff) + full lifecycle process | Personal accounts expected, but uniqueness & lifecycle less explicit |
| Access Principles | Combination of need-to-use, least privilege and need-to-know | Need-to-use principle is new; others already in BAIT/VAIT |
| Recertification | 6-monthly recert for CIF-related rights; annual for all others | BAIT/VAIT require “regular” review, but no fixed cycles or CIF link |
| Third-Party Access | Third-party staff fully covered by same IAM rules as internal users | External users controlled, but not framed as equal IAM population |
| Privileged & Emergency Access | Ad-hoc, need-to-use-only privileged access; strong auth; PAM encouraged | Strong admin controls exist, but PAM-like tooling becomes clear expectation |
Annex: Minimum contractual clauses
| Area/Topic | DORA Requirement | Difference to BAIT/VAIT |
|---|---|---|
| Form & Structure | Written, consolidated ICT contract incl. SLAs; formal documentation of amendments | BAIT/VAIT require written outsourcing contracts but no unified ICT contract format |
| Service Description | Clear, complete description of all ICT services incl. updates and revisions | BAIT/VAIT require service description, but less detailed and not ICT-specific |
| Locations | Explicit countries/regions of processing, storage, and service provision; advance notice of changes | Location clauses expected, but not mandatory at this level of specificity |
| Security Objectives | Contract must embed availability, integrity, confidentiality, authenticity requirements | Security clauses required, but DORA standardises and expands minimum scope |
| Data Access & Return | Guaranteed access, recovery, return and deletion of data incl. insolvency scenarios | BAIT/VAIT require reversibility, but without DORA’s insolvency-specific clarity |
| Incident Support | Mandatory support in ICT incidents at no or pre-agreed cost | Incident handling covered, but not formally defined as a contractual minimum |
| Cooperation with Authorities | Provider must fully cooperate with competent authorities | Regulatory cooperation clauses exist, but not ICT-specific or uniformly required |
| Training | Provider participation in ICT and resilience training | No equivalent requirement for provider training participation |
| CIF-Specific SLAs | Precise quantitative and qualitative SLA targets for critical/important functions | SLAs required, but no CIF-layered SLA precision in BAIT/VAIT |
| CIF Reporting | Enhanced reporting obligations on performance and risk developments | Reporting obligations exist, but less structured and not ICT-specific |
| CIF Business Continuity | Provider must have and test BCM plans aligned with the entity’s needs | BCM expected generally, but not mandated as a contractual CIF obligation |
| CIF Security Measures | Provider must implement ICT security measures matching regulatory expectations | Security required, but DORA formalises the minimum set |
| TLPT Participation | Provider must support/participate in TLPT for CIF | No TLPT participation requirement |
| Monitoring & Audit | Strong, unrestricted audit & information rights, incl. pooled audits | Audit rights required for outsourcing, but not uniformly across ICT services |
| Exit & Transition | Mandatory, tested exit support incl. orderly migration and transition periods | Exit required only for material outsourcing; intra-group relief exists |
| KPIs & Penalties | Defined KPIs, corrective actions and contractual penalties for CIF | Performance monitoring exists, but no KPI/penalty specificity |
| Subcontracting | Strict controls for subcontracting chains, notice periods, objection rights | Sub-outsourcing addressed, but far less detailed and not ICT-specific |
Source: BaFin, Supervisory statement: Guidance notes on the implementation of DORA for ICT risk management and ICT third-party risk management